Redundancy In the above example on the left, if Core 1 fails then the network is down and client A won’t be able to communicate with client B. In the example on the right, if Core 1 fails the network will say up as Core 2 is available and the Client can communicate through this. While this mitigates a single…
Category: Technology
4. VLANS
VLANS VLANs are used to isolate endpoints so you have better control over the traffic Default VLAN is VLAN 1 Devices in the same VLAN can communicate without routing. Collison Domains On a Layer 1 Hub, only one ethernet host on a particular segment may transmit at a time, otherwise there is a collision. This is controlled by an…
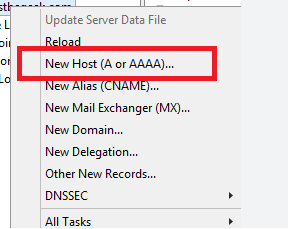
Creating Bulk DNS Records with PowerShell
PowerShell is a great tool for managing your repetitive tasks with DNS records. In this example I will show you how you can bulk import DNS records to Windows DNS servers. Populate a CSV with your device names and IP’s In PowerShell, import your CSV with the devices and IPs: #Import CSV $devices = Import-Csv “\\ServerPath\devices.csv” 3. Loop…
Automating Windows Server Updates with PowerShell
Introduction If you are anything like me, you probably get fed up managing Windows Server updates manually pretty quickly. Logging onto servers, checking for updates, installing them, rebooting them, trying to keep track of which servers have been updated, what updates were installed etc… etc… I wanted to automate the process but still have control over when the updates were…
16. Monitoring and maintaining Azure AD
Analysing and investigating sing-in logs to troubleshoot access issues Viewing logs Go to Azure AD -> Sign ins From here view and filter the sign in logs. You can see information like: – IP address – Date time – Applications – Login Status (success/failure) – location If you click on a log entry you get more information such as the…
15. Planning, Implementing Privileged Access and Access Reviews
Understanding Privileged Identity Management (PIM) Traditionally we use RBAC to manage administration privileges. We assign privileges to a role, then give a user that role. PIM takes things to another level What is PIM? PIM allow you to manage, control and monitor access to resources in your organisation. These resources include: Azure AD, Azure, O365, Intune etc… PIM allows you…
14. Planning and Implementing Entitlement Management
Defining Catalogs for Entitlement Management Microsoft provides us with a way a user can self-manage access rights to resources using “self-service”. With this method a user can logon and request access to a particular resource. A catalog is a group of resources like access packages. EG: if the company is doing a big marketing push, you could create a catalog…
13. Understanding Enterprise Apps and App registration for SSO
Configuring Custom SaaS Enterprise Apps with Token Customisation An example of this is: An app that runs on an onsite managed web server in the DMZ with an internet facing interface. EG: app1.spk.com We want to tie this to Azure AD for authentication so users go to Azure AD to get a token to access the app Azure AD has…
SC-300 Course: Microsoft Identity and Access Administrator (Study Notes)
I am currently studying for my SC-300: Microsoft Identity and Access Administrator exam. I am studying the content using John Christophers course on Udemy: https://www.udemy.com/course/sc-300-course-microsoft-identity-and-access-administrator/ On the following posts I will be uploading some of my study notes. This keeps me honest with making sure I keep have decent notes and hopefully they will be of help to other…
12. Managing Azure AD Protection
Understanding Azure Identity Protection with User and Sign in Risk policies Azure Identity Protection helps with the following tasks: Automate the detection and remediation of identity based risks (compromised accounts, phishing attacks etc…) Investigate risks using easy to find data Export risk data to third part tools for further analysis Identity Risk Detection Engines: Heuristics: the system monitors how the…