In this video Dr Rhonda Patrick and Dr. Satchin Panda discuss what ‘Time Restricted Feeding’ is and the benefits it has for the body. The video goes for 90 minutes but there is some great information in there. If you don’t have the time to watch the video, check out my notes below What is the circadian clock? Every…
Prioritise & Execute
We all know what its like trying to deal with that ever growing list of tasks. You get stressed just looking at the tasks and spend more time worrying about the list then actually working and dealing with any of the tasks. The following is some sound advice taken from the book ‘Extreme Ownership’ “Even the most competent of leaders…
How to (Easily) backup MS SQL Databases using Powershell
Backing up SQL databases with Powershell is quite useful and is probably easier than you think. This can be used in situations where you only have the SQL Server Express edition installed and can’t manage backups through the SQL Management Studio, or if you just want to do some one off backups Install SQLServer Powershell module 1. Open a Powershell…
5.4.14 Hop count exceeded – possible mail loop ATTR34
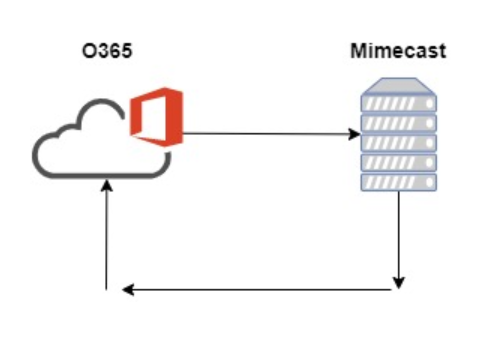
Issue: We recently configured our Exchange Hybrid setup and were experiencing this error when sending mail from our mailboxes migrated to Exchange Online to the mailboxes still on Premise that had the alias: @ourdomain.mail.onmicrosoft.com (On Premise Mailboxes had this alias setup in preparation for migrating to Exchange Online). Cause: We use Mimecast for our email filtering. The mail loop was…
How To Export Spiceworks Reports to HTML Using Powershell
Introduction This allows you to query the Spiceworks database and save the results as a HTML report. It uses the PSSQLite Powerhsell module and then the ‘ConvertTo-HTML’ command to output it to HTML. Step 1: Create your SQL Query It is best to run your test query’s against a copy of your Spiceworks database, not your live database. There are…
Powershell: Automating Exiting Users
Introduction I have being playing around with Powershell a lot more lately and trying to learn and utilise it as much as possible. One of the repetitive tasks we deal with is when a student exits the school. There are a number of steps in AD that have to be undertaken each time a student leaves. These include: Disable the…
PowerShell Resources
As a Sys Admin, I am probably a bit late to the party with how useful PowerShell can be. I have lately completed a couple of online courses about PowerShell and am trying to use it as much as I can in my day to day work. I am finding it incredibly useful in work and relatively easy to pick…
SQL Server Database Backups
Backups are crucial. You need to have the right backups in place to have your data covered in the case of any disasters. In this post I go through the different backup types and some of the different strategies for implementing them.
Security+ Course – 6.6 Cryptanalytic attacks
1. Brute Force Attacks Brute-force attacks are the simplest form of attack against a cryptographic system. In a brute-force attack, the attacker simply guesses repeatedly at the encryption key until he or she stumbles upon the correct value for the key and gains access to the encrypted information. Brute-force attacks can take a very long time to complete successfully, if…
Security+ Course – 6.5 Public Key Infrastructure (PKI)
1. Trust Models Requirements for Symmetric Key Exchange: The 2 parties must be confident that they are really communicating with each other and not an imposter The 2 parties must be confident that nobody is eavesdropping on the key exchange Asymmetric Cryptography Users don’t need to share their private keys Users can share their public keys freely Eavesdropping protection isn’t…