2.4.1 Wireless Networking WiFi standards are required so that any wireless device can connect to any wireless network around the world. WiFi uses transmitters and receivers in place of cables and connectors. WAPs (Wireless Access Points) connect wireless networks to wired networks. WiFi Standards 802.11 (1997) 2Mbps 802.11b (1999) 11 Mbps 802.11g (2003) 22 Mbps 802.11n (2009) 600 Mbps 802.11ac…
Security+ Course – 2.3 Managing Secure Networks
2.3.1 Firewall Rule Management Basic function of a firewall: someone from outside the network attempts to connect to a device inside the protected network firewall consults a ilst of rules maintained by the administrator if it finds a rule that matches the description of the attempted connection, it follows the action specified by that rule (it can allow it or…
Security+ Course – 2.2 Network Security Devices
2.2.1 Routers, Switches and Bridges Routers,switches and bridges are the building blocks of networks Switches A switch is hardware device on a network that connects devices on a network by using packet switching to receive and forward packets to its destination. Switches generally use MAC addresses to forward data at the Data Link layer (Layer 2). Some switches can forward…
Security+ Course – 2.1 TCP/IP
2.1.1 TCP/IP (Transmission Control Protocol/Internet Protocol) TCP/IP is a suite of communication protocols used to interconnect network devices on the internet. Internet Protocol Routes information across networks Provides an addressing scheme Delivers packets from source to destination Servers as a network layer protocol TCP & UDP These are transport layer protocols. TCP is responsible for the majority of internet traffic it…
Security+ Course – 1.6 Impact of Vulnerabilities
1.6.1 Vendor Vulnerabilities Every IT department relies on products and services provided by outside vendors (Servers, network equipment, software etc…) Product End of Life When a product reaches its end of life it introduces security concerns as they no longer provide patches/security updates for the product. End of Life Cycle End of sale:product is no longer available for sale but…
Security+ Course – 1.5 Vulnerability Scanning and Penetration Testing
1.5.1 Security Assessment Tools Vulnerability assessment tools come in 2 forms: Passive tools – monitor network traffic – observe system activity – provide reports but don’t interact with the systems (therefore no disruption to normal operation) Active tools – do interact with the systems to identify vulnerabilities and lack of security controls – does things like checking open ports or…
Security+ Course – 1.4 Application Attacks
1.4.1 Application Security Our increasing dependence on software makes it essential that we use software that is known to be secure and reliable. In one example of an application attack, a computer security expert hacked into a planes control system via the entertainment system by connecting his laptop to the device in his seat. He then used default username…
Security+ Course – 1.3 Understanding Attack Types
1.3.1 Denial of Service Attacks DoS Denial of Service attacks are a category of attack that disrupts the normal use of computing resources. they disrupt the availability of a web service by sending thousands or even millions of requests to a server, overwhelming it, and making it unable to answer any legitimate requests. These attacks can be difficult to distinguish…
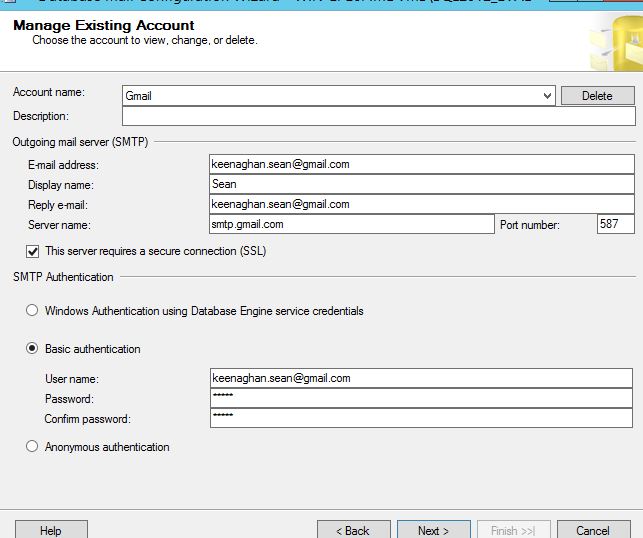
SQL Server: Configuring & Troubleshooting Database Mail
Database mail is great tool which allows you to send notification emails from your SQL Server. You can use to send notifications for things like backups, error, resource alerts etc… Configuring Database Mail Using the SSMS Wizard Go to Management -> Right Click on ‘Database Mail’ and select ‘Configure Database Mail’ Select the first option ‘Setup Database Mail by performing…