Contents [hide]
1. Legislative and Regulatory Compliance
Compliance Obligations
There are 4 main types:
- Criminal law: deter and punish acts detrimental to society (murder, theft, hacking etc…). This can result in jail time
- Civil law: designed to resolve disputes between civilians, organisations etc… This cannot result in jail time
- Administrative law: Facilitate effective government by allowing agencies to carry out their duties. They proved procedural rules for the operation of government
- Private regulations: Flow from contractual relationships. Govern activities between individuals and organisations
Federal Information Security Management Act (FISMA)
This is a law that governs information security matters for federal agencies and government contractors. It requires the creation of security programs throughout the federal government and provides details on the controls necessary to run information systems that are categorized as FISMA High, FISMA Moderate, or FISMA Low.
2. Security Frameworks and Reference Architectures
These are invaluable tools as they design security programs.
Security Frameworks: A collection of standards and practices designed to form a solid approach to information security. They’re high level, and they’re often focused on activities such as identifying risks and responding to attacks.
Reference Architecture: This provides a proposed design for security technology. This gets more into the technical details providing the specific controls that would achieve an organisations security objectives.
National Institute for Standards in Technology (NIST) Cybersecurity Framework
NIST publishes a cybersecurity framework that is free for anyone to use.
- Provides a common language for cybersecurity risks
- Helps organisations identify and prioritise actions
- Aligns security actions across control types
- Offers different value to different organisations
Link to the Framework: https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.04162018.pdf
3. Developing Security Baselines
Security baselines provide enterprises with an effective way to specify the minimum standards for computing systems and efficiently apply those standards across deployed devices.
Baseline Security Standard Elements
Baselines are generic that can apply to every device in the organisation.
The device:
- Must be Administered by a named individual
- is Protected against unauthorised access
- Doesn’t jeopardise other systems or data
- Remains under positive control of trained staff member
- Complies with data security requirements
Baseline requirements can also be more specific, such as requiring devices that store sensitive information to be encrypted. Another example of a specific standard may be that all Windows devices have the firewall turned on with all ports blocked except the necessary ports for the business System Configuration Managers automate policy deployment. You can create a template for these policies and then deploy it using Group Policy objects.
Monitoring is Critical
Once the policies are set you must monitor to make sure they are in place.
4. Leveraging Industry Standards
Most organisations don’t have the time to create their own security standards. Fortunately there are lots of industry standards available for use.
Sources of Industry Standards
Vendors
The companies that create the devices known the product better than anyone else and have a vested interest in making the product secure.
Government Agencies (NIST)
They have security baselines for different operating systems
Independent Organisations
These are 3rd parties that provide security advice. CIS is a good one:
5. Customising Security Standards
Organisations often start with the Industry Standard Baselines, then modify them to suit their own requirements. More stringent settings may be required based up data sensitivity or system criticality.
Instead of completely re-writing the standards you can reference them from your own. EG:
“Windows 2016 Server should be configured to the CIS benchmark dated 28/5/18, with the following exceptions…”
Document the reasons for any deviations.
6. Defense in Depth
Defence in Depth Principle: Organisations should use multiple, overlapping controls to achieve each of their security objectives. This is a layered approach that protects against the failure if any singular failure.
Examples of Use
Defence in Depth: Eavesdropping
– Encryption through VPNs
– Encryption at the application layer (using HTTPS)
– Segmentation with VLANs
Defence in depth: Access Control
– Network access control using strong authentication
– Role appropriate VLANs (using 802.1x technology to place users on correct VLAN)
– MAC Filtering
– Port security
Defence in Depth: Perimeter
The following devices could be used together to protect your internal network. If one device fails you still have some protection.
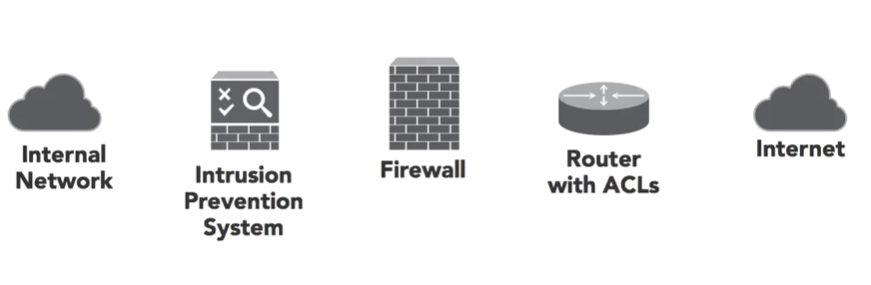
EXAM TIP: Remember to keep the defence in depth principle in the front of your mind during the exam!
7. Control Diversity
Diversity brings strength as people from different backgrounds bring different stories, styles and experiences to the table.
2 types of Cybersecurity Diversity
1. Control Type Diversity
This means using controls from different categories to control the same objective. An example of this may be trying to build defences against insider theft of sensitive information. The different categories here are Technical, Administrative and Physical. You could implement strategies from each of these to reach your objective. EG: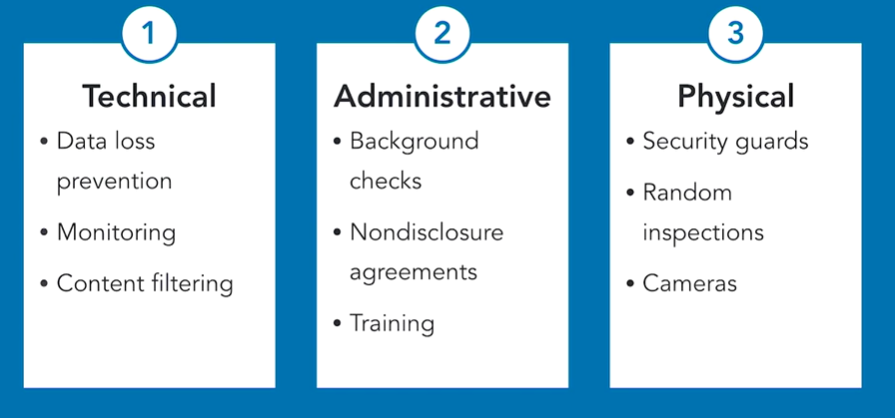
The strength comes from the fact that all these controls work in different ways.
2. Vendor Diversity
This reduces susceptibility to vulnerabilities. An example of this may be using different brand firewalls at different control points in a network. One could be at the perimeter of the internal network, the other could be in front of the data centre.
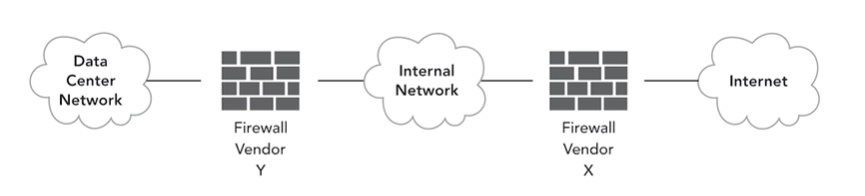
If there is a security flaw in Firewall X the attacker may gain access to the internal network. But as Firewall Y is a different brand they wont have access to the Data centre.
