Contents [hide]
1. Security Zones
Standard Network Zones
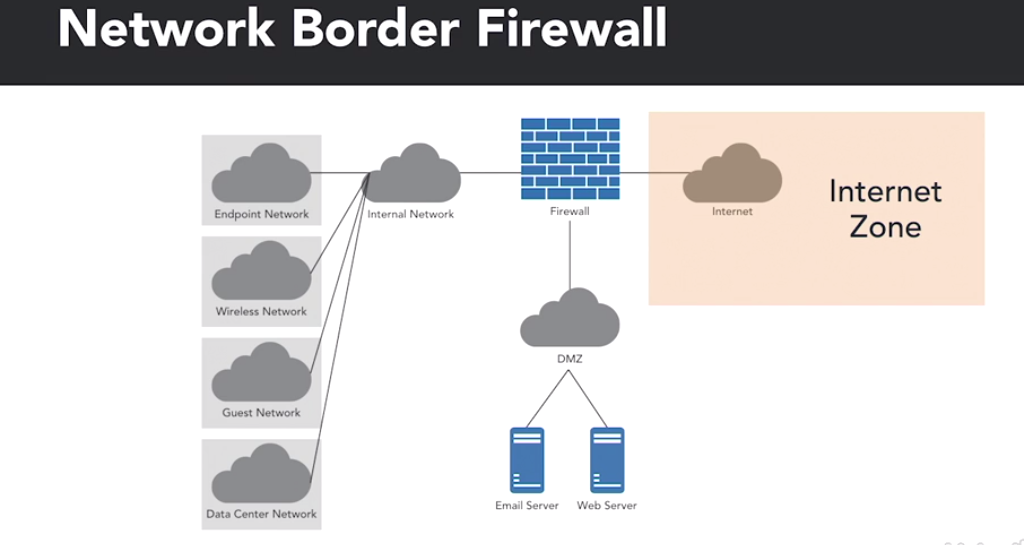
A network can be split up into different security zones. typically a boarder firewall will have 3 interfaces connecting to these different zones:
- Connection to the internet
- Connection to the internal network
- Connection to the DMZ (Demilitiarised Zone). This contains the public facing services (email servers, web servers). IF these get compromised the firewall still separates them from the internal network.
Special Purpose Networks
These are non standard networks setup in some organisations.
- Extranet: Intranet segments extended to business partners (maybe using a VPN)
- Honey Nets: decoy networks designed to attract attackers
- Ad Hoc Networks: temporary networks that may bypass security controls (when someone sets up a wireless access point and connects it to your network)
2. Public and Private Addresses
NOTE: there was more in IP addressing in section: 2.1 TCP/IP
Public IP Addresses
These are assigned by a central authority and are routable over the internet.
ICANN (Internet Corporation for Assigned Names and Numbers)
This is hte central authority that distributes large blocks of addresses to regional authorities for distribution.
IPv4 Address Scarce
There are no large blocks available today. There are only 4.3 billion possible addresses in the IPv4 range
Private IP Addresses
These ranges are available for anyone to use but they are not routable over the internet.
Private IP Address ranges:
- 10.0.0.1 – 10.255.255.255
- 172.16.0.1 – 172.32.255.25
- 192.168.0.1 – 192.168.255.255
Mix of Public & Private
Organisations generally have a mix of public and private IP addresses.
- Private addresses for their internal devices
- Public IP addresses for any internet facing services they may have such as web or mail servers
NAT (Network Address Translation)
This translates public IP addresses to private IP addresses at the boarder of the network (firewall).
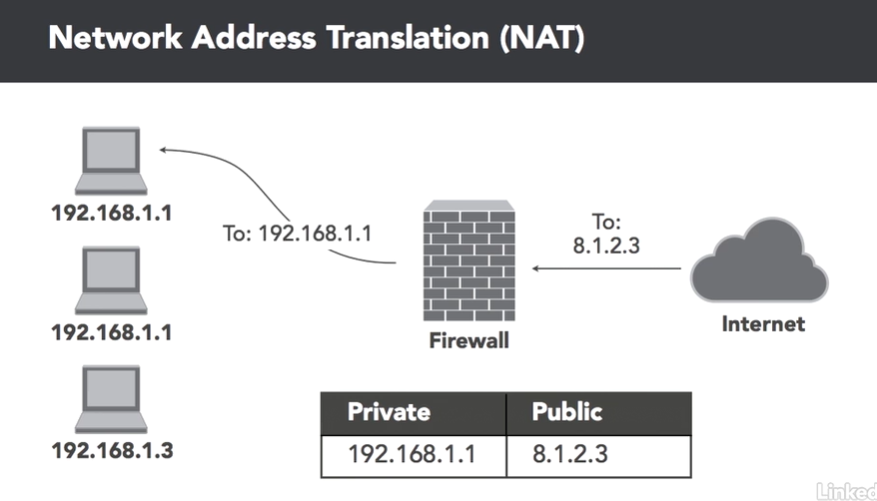
NAT and Security
NAT also has some security benefits. NAT:
- hides internal addresses from internet systems
- limits direct access to systems
- makes it difficult to identify the true origin of traffic
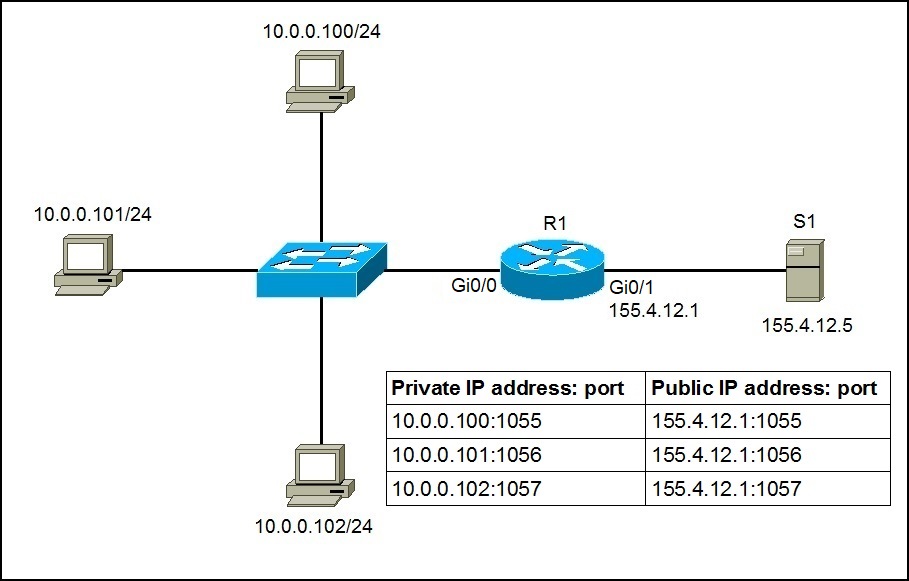
PAT (Port Address Translation)
The issue with NAT is it requires a public IP for every private IP accessing the internet. This is good for services like web and mail servers which need dedicated IPs, but over the top for most clients. PAT fixes this issue.
PAT allows multiple systems to share the same public IP address. Instead of assigning a public IP address to each device accessing the internet, it assigns a unique port number to each communication.
3. Subnetting
Subnetting is the process of dividing a large network into 2 or more smaller networks. This increases routing efficiency, enhances security, and reduces the size of broadcast domain.

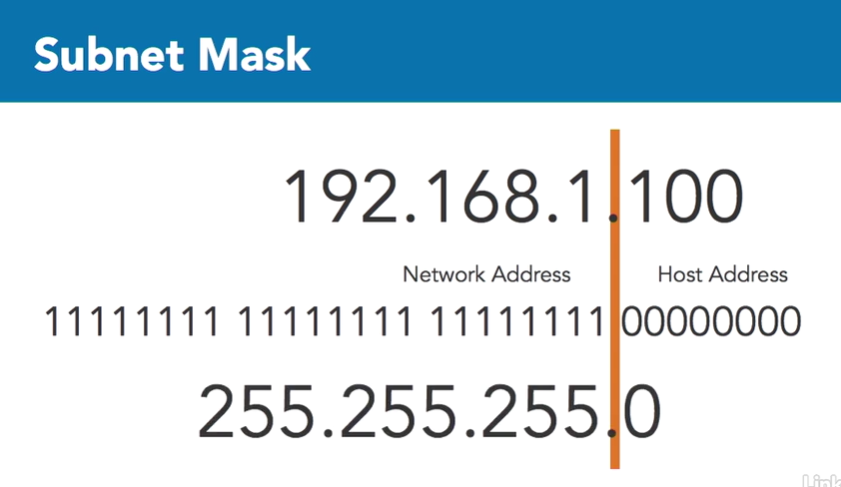
Subnet Mask
The subnet mask is used to divide the IP address into 2 parts:
- One part identifies the host (computer)
- the other part identifies the network it belongs to
4. VLANs (Virtual Lans)
VLANs allow us to separate systems on a network into logical groups based on function, regardless of physical location.
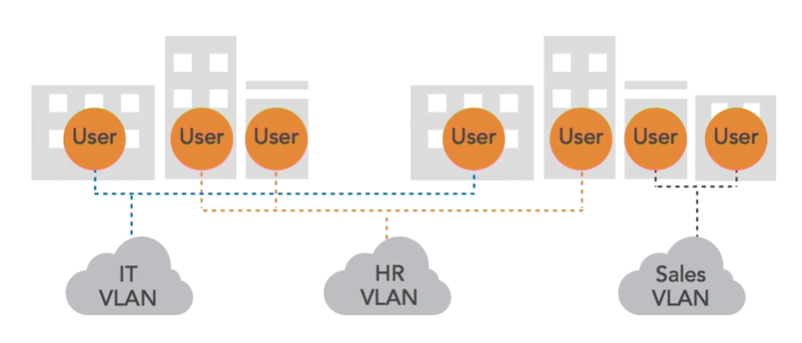
Devices on the same VLAN can communicate directly with each other, as if they are on the same switch. This is done using Layer 2 without involving routers or firewalls.
Improved security: Using VLANs improves security by reducing both internal and external threats. Internally, separating users improves security and privacy by ensuring that users can only access the networks that apply to their responsibilities. External threats are also minimized. If an outside attacker is able to gain access to one VLAN, they’ll be contained to that network by the boundaries and controls you have in place to segment it from your others.
For more on VLANs and their benefits see: https://www.summitir.com/2017/08/30/vlans-types-benefits/
6. Software Defined Networking (SDN)
Software-defined networking technology is an approach to network management that enables dynamic, programmatically efficient network configuration in order to improve network performance and monitoring making it more like cloud computing than traditional network management. https://en.wikipedia.org/wiki/Software-defined_networking
Network Functions
- Control Plane: this is responsible for making switching and routing decisions and the flow of data throughout he network. It can reroute packets when a device fails or a network segment is congested.
- Data plane: this is the mechanics of moving data around. It carries out the instructions of the control plane.
SDN separates the control plane from the data plane. Instead of each router or switch making decisions about the flow of packets, these decisions come from an SDN controller. The controller is where administrators and algorithms make decisions about network routing and the controller reaches out to each device on the network and programs it to carry out these instructions. The SDNcontroller implements the control plane of the network, the routers and switches carry out the data plane.
SDN makes the network programmable. Developers write code to make network changes. EG: if a program needs more bandwith, it can reach out and reconfigure the network to provide more bandwith. It can then release it when the bandwidth is no longer required.
Security Benefits
- Allows granular network configuration
- Facilitates faster response to security incidents. EG: if the network is under DDoS it can shutdown that port and put the host in quarantine.
Cons
SDN in creases network complexity.
7. Port Isolation
This is a network security technique that is useful when users of the network do not trust each other and are not trusted themselves.
Port isolation restricts traffic from a source port to a single destination. EG: this could be setup so that a device connected to a port on a switch can only communicate with the uplink on the switch, not other ports that have devices connected. This prevents the devices on the same switch from communicating with each other. A use case for this may be in a hotel. Each guest can connect to the switch and get internet access, but they cannot communicate with other guests connected to the switch.
This typically not effective in a corporate network.
Exam tip: Port isolation and private VLANs are the same thing.
