Contents [hide]
1. Industrial Control Systems (ICS)
ICS monitor and control industrial processes. Hackers love to target ICS for the following reasons:
- these attacks often have dramatic implications. EG: taking down a city electricity or water system
- these systems are often not well secured
- these systems are less likely to be patched and updated. In fact, some ICS system manufacturers advise their customers not to update the control systems and their sensors
ICS Types
- Supervisory Control and Data Acquisition (SCADA)
These are often used in industry for the remote monitoring of systems such as gas pipelines, power production and water control systems. They typically include sensors known as remote telemetry units, which provide reports back to the central data collection system and provide some level of control. Attacks on SCADA could happen at the sensor end (to send back incorrect feedback) or the controller end. - Distributed Control systems (DCS)
These are often used to control production lines for things like cars, electronics and even food products. DCS use a combination of sensors and feedback systems to control and adjust processes as they receive feedback. These also have multiple attack points, similar to SCADA. - Programmable Logic Controllers (PLC)
These are special purpose computers designed to handle input and output reliably. They are typically designed to run in difficult environments (temperature, vibrations etc…). PLC’s connect to Human Machine Interfaces (HMI) so humans can operate them. This is generally not a monitor but buttons and lights built into them.
SCADA System Attacks
In 2000 a man hacked into the sewage system in Maroochy, Queensland, and released millions of litres of raw sewage into local parks, rivers and even the grounds of the Hyatt Regency hotel.
This was a revenge attack as his job application was rejected.
https://www.theregister.co.uk/2001/10/31/hacker_jailed_for_revenge_sewage/
2. Smart Home Technology
Embedded computers are now part of our everyday life. Smart technology is everywhere. Smart devices are computer controlled and connected to the network.
Exam tip: the security + exam uses the term embedded systems to refer to Smart devices
Types of Smart devices:
- In our home: wireless printers, wireless game controllers, sprinkler systems, lighting systems, home assistants
- In cars: connectivity systems, Bluetooth
- Wearable devices: items used to monitor health and fitness
Together these devices are known as the internet of things (IoT).
Security Challenges
- it is often difficult for the consumer to update the devices. They may not even know they need to be updated.
- Devices connect to the home and office network. If they are compromised they have access to the network.
- Often these devices connect back to cloud services for command and control. This creates a potential path or hackers into our network.
Attacks
In 2015 hackers took control of a Jeep Cherokee (in an experiment). They were able to control the AC, on board entertainment system, and even the acceleration and brakes.
https://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/
3. Securing Smart Devices
Regularly update the Smart device software
Some devices have automatic updates that install without the users knowing or intervention. But some are manual and require that the user check for updates and download them when available.
Security Wrappers
In some cases it is not possible to patch the systems for a known vulnerability. In these cases you can use a security wrapper. In this approach the device does not have direct access to the network but instead it is reached through the wrapper system that monitors input and output and only passes vetted requests from network systems. It is like a mini firewall for the embedded device.
4. Secure Networking for Smart Devices
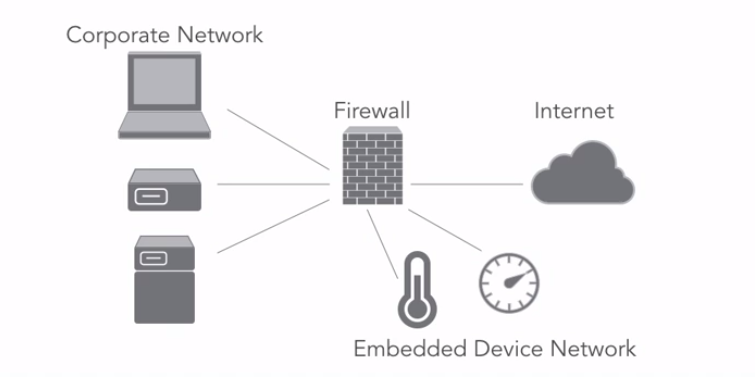
Network Segmentation
Place untrusted devices on their own network segment. This way they have no access to trusted systems.
Exam tip: this is the most important control you can put in place for embedded devices
Air Gapping
Air gapping take network segmentation to the extreme degree and it is appropriate for use in the most sensitive cases, such as the control system for a nuclear reactor or other situations where there are life safety issues at stake. An air gap for a network means that there is no connection between the air gapped network and any other network. If a user needs to access the air gapped network they have to physically visit a machine on this network.
Application Firewalls
Embedded systems that have web interfaces are susceptible to many of the same web applications attacks that we find on more complex systems. They can be vulnerable to SQL injection, buffer overflows, and cross-site scripting attacks. Application firewalls, when placed in front of these systems, monitor inbound traffic for signs of malicious activity, and when they detect this type of hostile traffic they can block it before it reaches a potentially vulnerable embedded device.
Exam tip: embedded security device controls are effective for securing mainframes as well
5. Embedded Systems
There are 2 main types of embedded systems:
- System on a Chip (SOC): this is an entire embedded system packaged into a single chip. This typically includes a microprocessor, memory, clock, power management, network interfaces etc…
- Real Time Operating System (RTOS): these power the internet of things by providing a secure and reliable environment for processing IoT code. Modern server and desktop systems, such as Windows, are large and complex, designed to perform a wide variety of functions. This complexity sometimes leads to problems, such as processes hanging or whole OS crashes.
In many IoT environments this is simply unacceptable. EG: you wouldn’t want your self driving cars safety system to crash because you were watching a movie that took too much memory. The real time operating system is designed to provide resources to the highest priority tasks as they occur, and as the name implies to work in real time. This is critical for IoT systems that drive high-value processes or affect human safety.
