Contents [hide]
1. Site and Facility Design
Sites to be protected:
– Data Centre
– Server rooms
– Media storage facilities (where you keep your offsite backup media)
– Evidence storage locations
– Wiring/Switch cabinets/closets (could be used for eavesdropping or getting access to the network)
You should perform inventory of all sensitive sites and audit the security controls.
2. Data Centre Environmental Controls
The equipment in data centres is very sensitive to the environment.
Cooling
Electronic equipment generates a significant amount of heat and if a data centre does not have appropriate cooling it can become extremely hot. Excessive heat can damage servers and other equipment and dramatically reduce its expected life. Conventional wisdom about data centre temperatures has changed over time. They used to be kept very cold (you needed jackets to go into them) but this was very expensive in electricity bills. Computer equipment has become more efficient and more tolerant of heat, so the standards have relaxed. The recommended data centre temperature these days is between 64.4 and 80.6 degrees F( 18 – 27 C)
Humidity
High Humidity: this leads to condensation that may damage electronic equipment.
Low Humidity: this leads to static electricity that may damage electronic equipment.
Dew Point Range
The environmental specialists measured data centre humidity using the dew point, and recommend maintaining the facility at a dew point somewhere between 41.9 and 50 degrees Fahrenheit (5.5 – 10 Celsius). That’s the sweet spot that keeps both condensation and static electricity away.
Data Centre Design
Servers draw cool air in the front and expel hot air out the back. This keeps cold air flowing over the components.
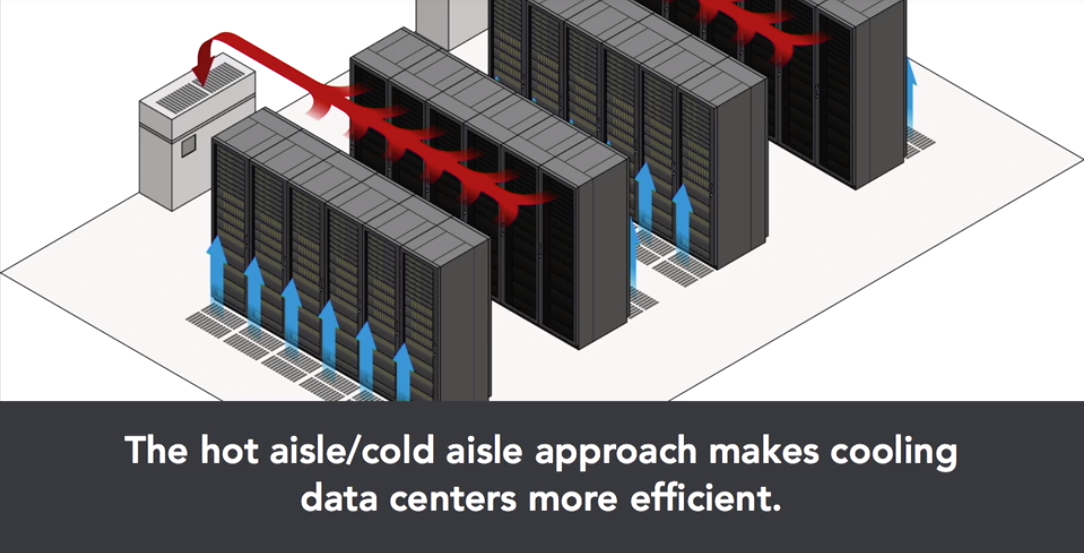
Hot aisle/cold aisle approach
In this approach you place racks of opposite sides of an aisle to face each other. This leads of course to the backs of racks facing each other as well. When laid out in this manner, aisles alternate purpose between being a source of cold air or an exit point for warm air. HVAC designers can use this to their advantage, pumping cool air into the cold aisle and pulling warm air out of the hot aisle.
EXAM TIP: there may be questions asking about data centre setup and where you would put the cooled air distribution vents (front of servers) or the hot air return vents(back of servers).
3. Data Centre Environmental Protection
Data centre managers must also be prepared for more serious situations such as fire, flooding, and electromagnetic interference.
Fire
Fire is a grave threat in a data centre. Data centres must have fire suppression systems in place.
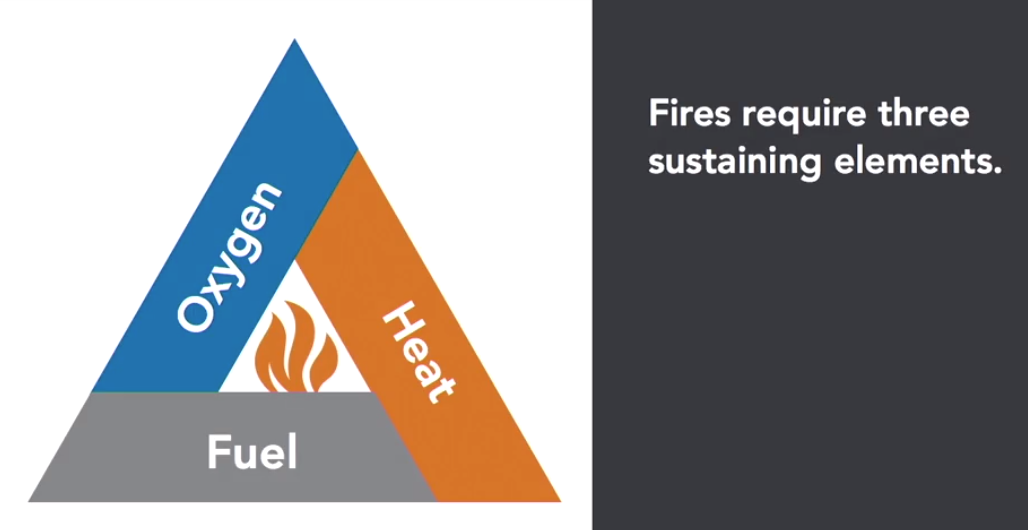
If you can deprive a fire of any of these elements, it will go out.
Fire Extinguishers
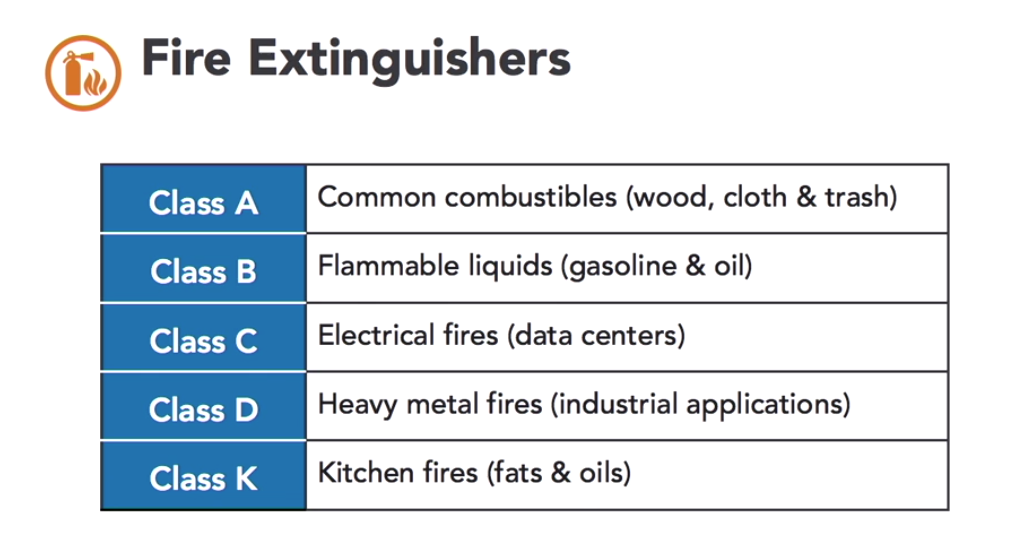
EXAM TIP: be able to identify the classes of fire extinguisher on the exam
Water Based Sprinkler Systems
Data centres generally have a facility wide water based sprinkler system. But this is a risky approach as water is very damaging to electronic equipment. An accidental discharge or burst pipe can lead to disaster.
Types of water based sprinkler system:
1. Wet pipe approach: the pies are filled with water constantly. If the pipe bursts or leaks the data centre can be flooded.
2. Dry pipe approach: There is no water in the pipes until there is an actual emergency. There is a valve that prevents water from entering the pipes until a fire alarm is triggered.
Chemical Systems
These can deprive the fire of oxygen. This can be very dangerous, you obviously don’t want to do this with people in the room!
Flooding
Try to route plumbing so that a leak wont effect the data centre. You also want to have the data centre in an area that is unlikely to be affected by a flooding natural disaster.
Electromagnetic Interference (EMI)
Every piece of electronic equipment generates electromagnetic radiation and this poses two risks. First, EMI can interfere with the normal operation of systems, causing them to malfunction. Second, if an attacker is able to capture the EMI emanations from a facility, he or she may be able to reconstruct the keystrokes or other activity that generated the electromagnetic signals and this may contain sensitive information.
For this reason, data centre managers should monitor for electromagnetic interference and consider designing their facilities to minimize this type of radiation. Faraday cages are one way to control EMI but they are complex and expensive. They require building a metal cage around electronic equipment that prevents electromagnetic waves from entering or leaving the cage. You will rarely see faraday cages used outside of classified government facilities or as protection for extremely sensitive scientific instruments.
4. Physical Security Control Types
Categories of Physical Control Types
Category 1: Intended Effect Categories
- Deterrent controls: this is a show of force warning people not to enter. EG: “Beware of the dog” sign
- Preventive controls: this are designed to actually block intruders from entering the area. EG: biometeric readers when entering sensitive areas
- Detective controls: these are intended to alert security staff to a potential or actual security violation. EG: CCTV
Category 2: Mechanism of Action
- Technical Controls: uses technology to deter prevent or detect security violations. EG: a motioned sensor alarm system
- Administrative controls: these do not rely on technology but upon business processes to enhance security. EG: running background security checks on security guards
Category 3: Compensating Controls
- Fills gaps in other security areas. EG: if you have a barb wire fence surrounding the building, but there is a gate that people could climb over. You may put a security guard on the gate.
EXAM TIP: Physical security controls are a common problem area for candidates taking the exam
5. Physical Perimeter Security
Door lock types:
- Physical key: ensure to keep a log of who has the keys
- Cipher lock: this uses a programmable keypad
- Bio-metric locks: these locks grant access based on a unique body trait of the person trying to open it. This can mean either your retina or your fingerprint.
- Card readers: these locks use programmed access cards (magnetic strips cards, prox cards) to grant access to an area.
Challenge: securing area between public and secure
Tailgating can be a real problem here. A mantrap can fix this issue. It is like an airlock between the secure and public area. Once someone comes through the public door that door closes behind them. The secure door wont unlock until they have authorised access (using biometric, card etc…) and when there is only 1 person in the room (to stop tailgating). It uses technology such as cameras to ensure there is only 1 person in the area.
Maintain access lists carefully!
Other methods of security:
- fences to prevent intrusions by foot or vehicle
- Cages may be used to separate equipment in data centres
- Proper lighting and security signs can be a deterrent
- Network cables must be secured away so someone can not easily access them and get onto your network
6. Visitor Management
Visitor procedures:
- Describe allowable visitor purposes
- Explain visit approval authority
- Describe requirements for unescorted access
- Explain role of visitor escorts
- Log all visitor access to secure areas
- Visitors should be clearly identified with distinctive badges
7. Hardware Physical Security
Mobile Devices
Mobile devices are valuable and easy to steal. They may give the thief access to sensitive data. Encryption prevents sensitive data on mobiles. This limits the damage that may happen after a theft of a mobile device.
Cable locks protect laptops and other portable devices from theft.
EXAM TIP: remember to secure the other end of the locking cable!
Store mobile devices not in use in a secure method such as a vault or safe. Or use a locking laptop cabinet.
Use security tags on your devices. These leave a permanent mark on the device if someone tries to remove them. This decreases the value when someone goes to sell the device. You can also have the company name on it so it easy for someone to return the device If they find it.
